Time Manipulation Bypasses Enrollment Date Restrictions
Hey guys! Today, we're diving deep into a fascinating bug discovered in the system: the ability to bypass enrollment date restrictions by simply manipulating the system's time and date. This issue can lead to the creation of invalid student entries and, trust me, it gets pretty weird when you set the date back to normal. Let's break down what this means, how it happens, and why it's a significant problem.
Understanding the Issue
At its core, this bug allows users to circumvent the intended enrollment date restrictions by setting their system's time and date to a future date. Imagine you're trying to add a student with an enrollment date that should be within a specific timeframe. By tweaking the system clock, you can trick the application into accepting entries that it normally wouldn't. This time manipulation results in what we call an invalid student entry, which can cause a cascade of issues down the line.
The Weirdness Factor
Now, here's where it gets interesting. Once you've created this invalid entry and then set the system time back to normal, the application's display of the student list goes haywire. We're talking about visual glitches, incorrect data, and an overall buggy experience. It's like the system is struggling to reconcile the past (the actual date) with the future (the manipulated date). This discrepancy highlights a critical flaw in how the application handles date validations and data integrity.
Tested on Windows
For those of you who are curious, this bug was specifically tested and confirmed on a Windows environment. While this doesn't necessarily mean it's exclusive to Windows, it does give us a clear starting point for investigation and patching efforts. Knowing the platform where the bug was identified helps developers narrow down potential causes and focus their debugging efforts more effectively.
Steps to Reproduce
Okay, let's get into the nitty-gritty. If you're a tech enthusiast or a developer, you might be interested in reproducing this bug yourself. Here’s a step-by-step guide on how to do it:
-
Go to your system settings and manually set the time and date to a future date. The key here is to change the month. This manipulation is crucial because the bug seems to be triggered by changes in the month rather than just the day. You can also play around with timezones that affect the displayed month – that might just do the trick too.
-
Add an entry with the enrollment date set to the future. Use a command like the one below for reference. This command simulates adding a student with details such as name, phone number, email, address, and module:
add n/John Doe p/98765432 e/johnd@example.com a/John street, block 123, #01-01 m/1127 -
Set the time back to normal. Once you've added the entry with the future date, revert your system time to the correct, current date and time. This step is essential to trigger the display bug later on.
-
Exit the program. Close the application completely. This ensures that the changes you’ve made are properly saved (or, in this case, improperly saved).
-
Launch the program. Reopen the application. This fresh start will allow you to see the bug in action.
-
List student entries. Navigate to the section where student entries are displayed. This is where the magic (or rather, the bug) happens.
-
Observe the bugged student display. You should now see the student display acting up. This could manifest as incorrect dates, missing information, or other visual anomalies.
Visual Evidence
To give you a clearer picture, here’s an image of what the bug looks like in action:
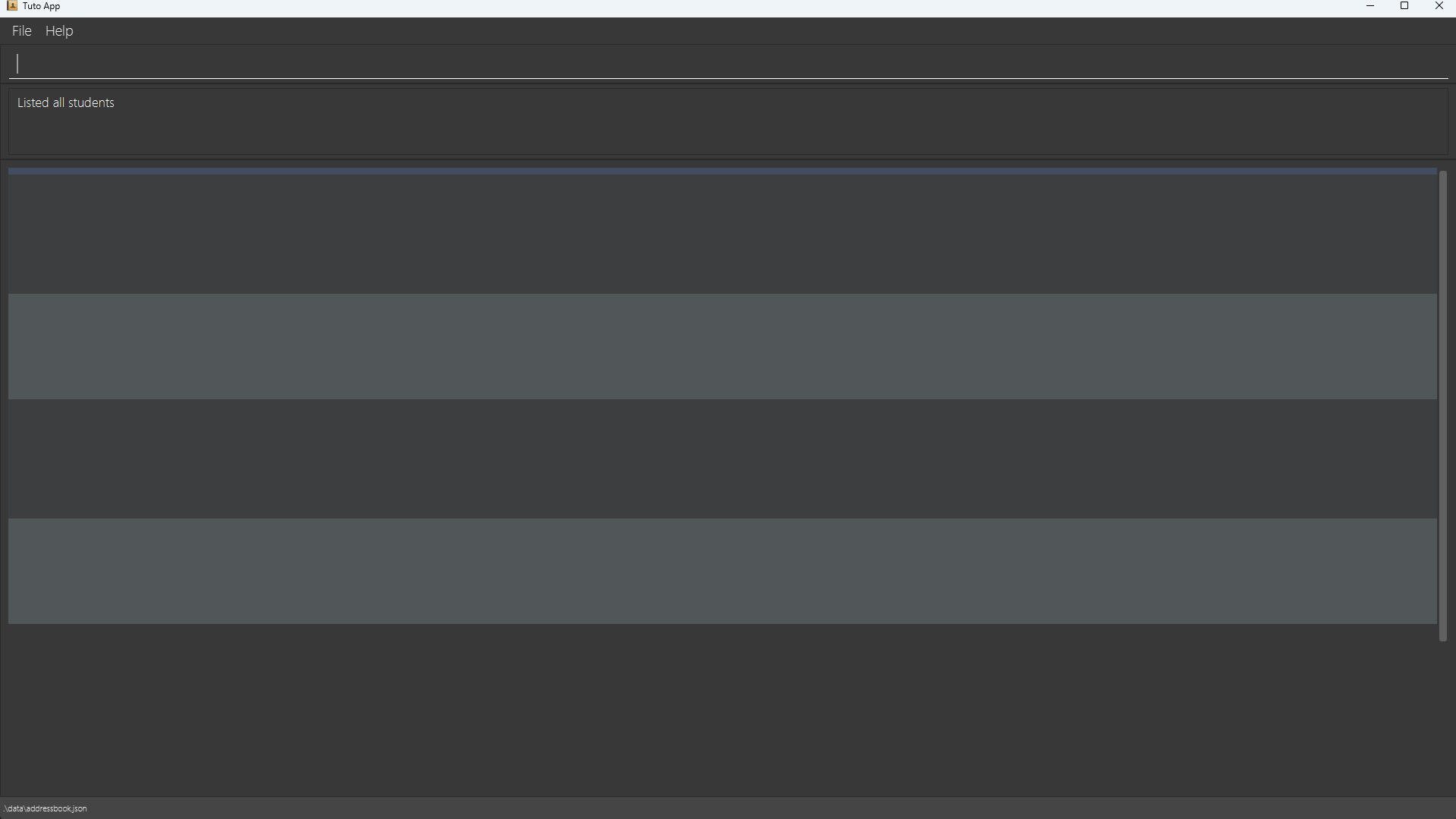
As you can see, the display is clearly not functioning as intended. This visual evidence underscores the severity of the issue and the importance of addressing it promptly.
Severity and Type
This bug has been labeled with severity.Medium and type.FunctionalityBug. Let's break down what that means:
- Severity.Medium: This indicates that the bug is significant enough to cause noticeable issues but doesn't completely cripple the application. It's more than a minor cosmetic problem but less severe than a critical crash or data loss issue.
- Type.FunctionalityBug: This means the bug directly impacts the core functionality of the application. In this case, it affects the ability to correctly manage and display student enrollment data.
Understanding these labels helps prioritize bug fixes and allocate resources effectively. A medium severity functionality bug is something that needs to be addressed in a timely manner to prevent further complications.
Why This Matters
So, why is this bug such a big deal? Well, imagine a scenario where accurate enrollment data is crucial – like in a school or university setting. If someone can manipulate the system time to add students with incorrect enrollment dates, it can lead to a whole host of problems:
- Inaccurate Records: The most obvious issue is that the student records become unreliable. Enrollment dates are important for various administrative tasks, and incorrect dates can throw everything off.
- Scheduling Conflicts: If enrollment dates are tied to course scheduling, incorrect dates can lead to students being enrolled in courses they shouldn't be, or missing deadlines.
- Reporting Errors: Many institutions rely on accurate data for reporting purposes. If the data is flawed due to manipulated enrollment dates, it can lead to compliance issues and incorrect statistics.
- Security Concerns: While this bug isn't a direct security vulnerability, it highlights a potential weakness in the system's validation mechanisms. This could be a stepping stone for more serious exploits in the future.
In short, this bug undermines the integrity of the entire enrollment system. It's crucial to fix it not just for the sake of visual appearance, but for the reliability and accuracy of the data itself.
Potential Fixes and Preventative Measures
Now that we've dissected the problem, let's talk about solutions. How can we fix this bug and prevent it from happening again?
- Server-Side Date Validation: The most robust solution is to validate enrollment dates on the server side. This means that the application should rely on a trusted time source (like a network time server) rather than the client's system time. This prevents users from manipulating the date and time to bypass restrictions.
- Input Sanitization: Implement strict input sanitization to ensure that all dates entered by users are valid and within the allowed range. This can involve checks for future dates, past dates, and other date-related constraints.
- Database Integrity Checks: Regularly run database integrity checks to identify and correct any inconsistencies or anomalies in the data. This can help catch any invalid entries that might have slipped through the cracks.
- Client-Side Validation (with Caveats): While client-side validation alone isn't sufficient, it can provide an initial layer of defense. However, it should always be paired with server-side validation to prevent bypasses.
- Regular Security Audits: Conduct regular security audits to identify potential vulnerabilities and weaknesses in the system. This proactive approach can help prevent bugs like this from making their way into production.
- User Education: Educate users about the importance of not tampering with system time and date settings. While this won't prevent malicious attempts, it can help reduce accidental occurrences.
By implementing a combination of these measures, we can significantly reduce the risk of enrollment date manipulation and ensure the integrity of the system.
Conclusion
Alright, guys, we've covered a lot of ground here. We've explored the bug that allows bypassing enrollment date restrictions by manipulating system time, the steps to reproduce it, the severity and type of the bug, why it matters, and potential fixes. This bug serves as a valuable reminder of the importance of robust date validation and security measures in any application that handles sensitive data.
Remember, a seemingly small bug like this can have significant consequences if left unchecked. By understanding the issue and implementing appropriate safeguards, we can build more reliable and secure systems. Keep exploring, keep questioning, and keep coding! You never know what interesting bugs you might uncover along the way. And who knows, maybe you'll be the one to come up with the next big fix! Until next time, happy bug hunting!